Cloud service providers offer virtualized environments in a multi-tenant configuration. When a number of subscribers are running their programs and storing their data in a multi-tenant environment, there is always a tinge of worry regarding data spoofing or data leakage etc. Further, there’s always an apprehension about the uncertain location of the infrastructure especially the data storage and the absence of awareness of rules that are globally and locally accepted about data security and privacy. Unauthorized access, shared infrastructure and multi-tenant environment – all pose a number of vulnerabilities. But, cloud services today are becoming a norm and many businesses and enterprises are moving their workloads to public clouds and expect services with security compliance as tight as on-premise infrastructures.
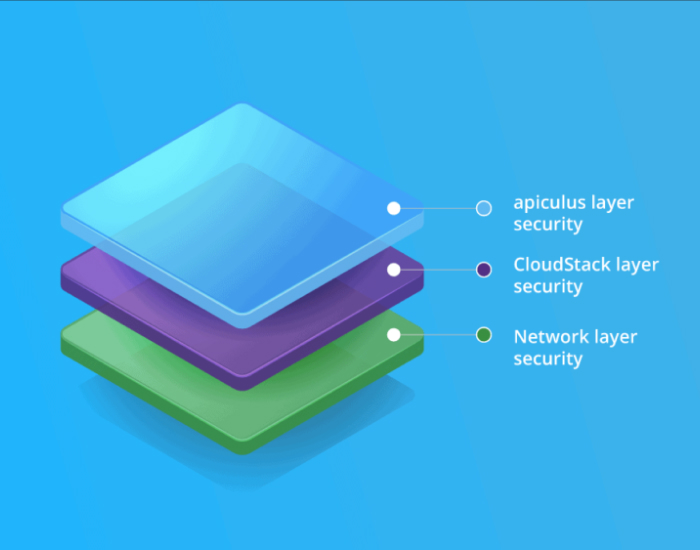
However, building security in a cloud infrastructure from scratch requires planning to articulate where controls are enforced – right from the design phase. The key to effective cloud security is improving the overall posture and to ensure that security is built progressively beginning with the network layer, the CloudStack orchestration layer and the apiculus layer (Cloud Management Platform). Throughout design and deployment, each component is secured, built and hardened to meet the highest standards for availability, resilience, performance and security to make the services continuously available – uninterrupted.
Let’s take a look at the security considerations for a Apache CloudStack based public cloud:
Network layer – the physical network
The physical network elements provide a baseline for the security of the entire cloud infrastructure. Identifying elements and ensuring that each one is critically assessed for security against known and unknown attacks is the first step. It is essential to reduce the attack surface and enforce a network security model that eliminates unauthorized access within it. A host of security activities are performed at the network level to diagnose any loose ends and make recommendations to fix it.
Apache CloudStack – the orchestration layer
Apache CloudStack is generally considered secure out of the box. It includes a number of built-in security features that have the capability of protecting both system VM traffic as well as management traffic separately. It also provides options for using keys to encrypt the cloud platform databases. The tenants are arranged in a hierarchical manner into domains and each domain can be dedicated to the use of particular segments like enterprise or retail. It also offers complete audit trails and logs any action that is taken by any user. To tighten the security further, all the infrastructure modifying operations and settings are available only to the root CloudStack user. The management servers are on a separate network and are inaccessible by the end users. The system VMs are well protected and can only be accessed using keys from the underlying hypervisor over the link-local network.
apiculus – the cloud management platform
apiculus forms the user facing layer and is the only layer that users can directly interact with. It’s hence essential to understand how this layer can help tighten the security of your cloud service. apiculus has built-in security services such as user identification, authentication, access enforcement, key management and such other measures to reinforce security for your cloud service.
As one of the leading firms facilitating the setup of in-country public cloud services based on CloudStack for various providers in both emerging as well as advanced markets, we understand the security implications of building a cloud service from ground up. We have also published a Whitepaper that outlines our approach to security compliance while we help build domestic public clouds and help local service providers to build appropriate defence mechanisms to safeguard their customer’s (subscriber’s) data, critical workloads and applications.
You can read the complete Security Whitepaper here.
If you would like to take a tour of our Cloud Management Platform – request a demo here. You can contact us here and our representative will get in touch with you!