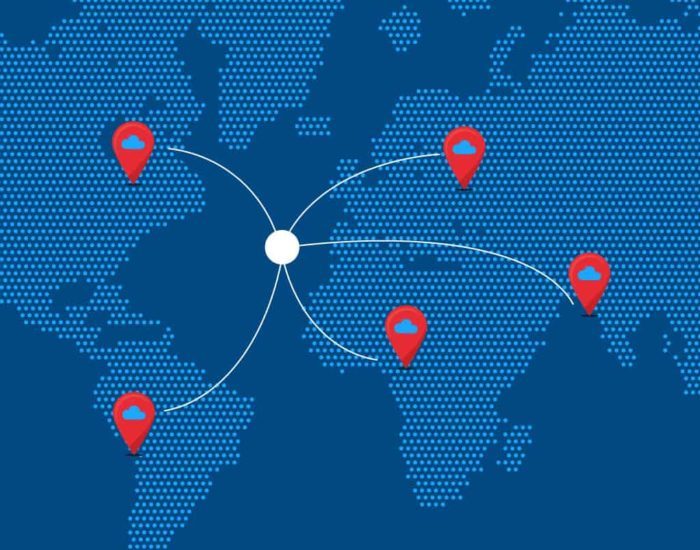
Cloud service providers in regions in emerging markets often start with a small setup, which is predominantly circled around a single data centre. This helps them test the […]
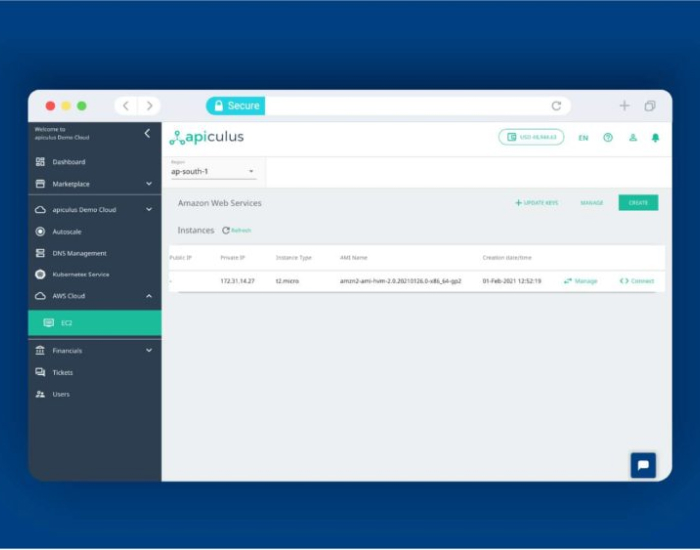
More power to AWS Integration – now create EC2 instances within apiculus!
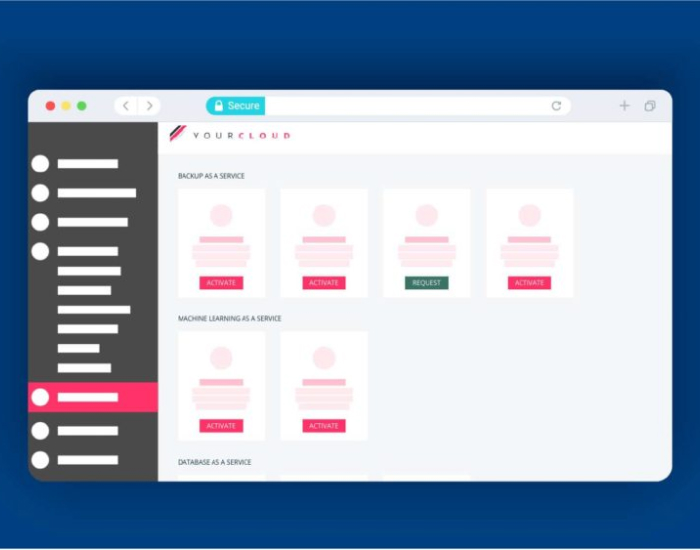
Background: With AWS (Amazon Web Services) integration on apiculus, cloud service providers can offer AWS subscription packs from their Cloud Marketplace, define the pricing for these subscription packs […]
Apiculus, a white-label solution – beyond branding
Specially tailored to suit a service provider’s requirements, white labelling on apiculus consists of a completely rebrand-able solution. With apiculus, you can customize and add your preferred colour […]
Reseller and Channel Management on apiculus to effectively manage your customer acquisition channels
Cloud service providers who diversify their sales channels by partnering with a network of resellers now have an effective means to streamline their accounts and billing directly from […]
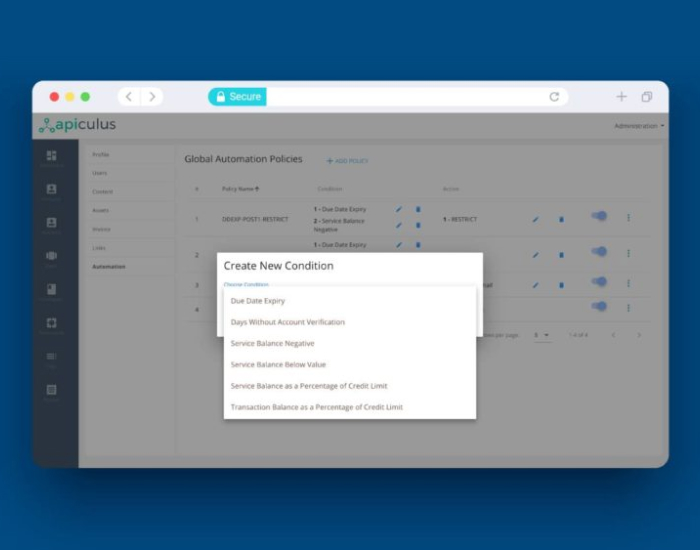
Automated dunning policies on apiculus to better manage your billing
Dunning is a part of a broader credit control system to better manage billing/finances of your cloud service. Periodical correspondence with customers/subscribers about delayed invoices, dwindling service balances […]
Apiculus Dashboards – Measure What Matters
The ability to pull key information and consolidate it for all the data sources that matter is not only a nice to have but a must-have feature for […]
Marketing and Analytics Stack Integration
Understanding user behaviour, behavioural clickstreams, user preferences and similar insights empower the product and marketing decision-making process. It also helps measure and understand the ROI based on solid […]
Resell AWS from your own cloud with AWS-Apiculus integration
The Public Cloud Market is massive – but is currently dominated by the three major players – the hyperscalers – Amazon Web Services (AWS), Microsoft Azure and Google […]
Role-based Access Control on Apiculus SP Administration Console
Security is more easily maintained when limiting unnecessary access rather than managing permissions for individual accounts or users. Managing and auditing network access is an essential security aspect […]